Ethical Hacking

Ethical hacking, also known as penetration testing or white-hat hacking, refers to the practice of intentionally and legally exploiting computer systems, networks, or applications with the permission of the owner. The goal of ethical hacking is to identify and address vulnerabilities in a system's security before malicious hackers can exploit them.
Ethical hackers, often employed by organizations or hired as independent consultants, use the same techniques and tools that malicious hackers might employ to discover weaknesses. However, the key difference is that ethical hackers operate within a legal and ethical framework. They have the explicit authorization to probe and assess the security of a system, and their activities are conducted to improve the overall security posture.
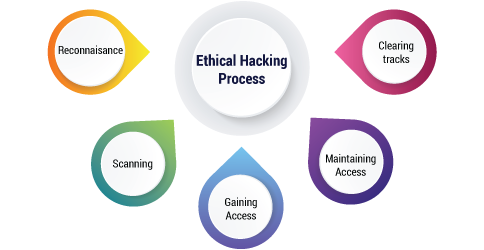
The ethical hacking process typically involves several key steps:
Authorization: Ethical hackers must obtain explicit permission from the system owner before conducting any testing. This involves a clear understanding of the scope and limits of the testing.
Reconnaissance: This phase involves gathering information about the target system, such as its architecture, networks, and potential vulnerabilities. Ethical hackers may use both passive and active methods to collect data.
Scanning: Ethical hackers use scanning tools to identify live hosts, open ports, and services running on the target system. This helps them pinpoint potential entry points for attacks.
Gaining Access: Ethical hackers attempt to exploit vulnerabilities to gain unauthorized access to the system. This step is crucial for identifying and understanding the impact of potential security flaws.
Maintaining Access: Once access is gained, ethical hackers may attempt to maintain it to assess the effectiveness of security measures and to identify any weaknesses in monitoring or detection systems.
Analysis: Ethical hackers analyze the results of their testing, documenting vulnerabilities, and providing recommendations for improving security.
Reporting: A comprehensive report is generated, detailing the findings, the severity of each vulnerability, and recommendations for mitigating or fixing the issues. This report is then shared with the organization's management and IT team.
Web application security

Web application security is a critical aspect of overall cybersecurity, especially considering the increasing reliance on web applications for various online activities. Here are key concepts and practices related to web application security:
Secure Coding Practices:
Input Validation: Validate and sanitize user inputs to prevent common vulnerabilities like SQL injection and Cross-Site Scripting (XSS).
Output Encoding: Encode data before displaying it to prevent XSS attacks.
Session Management: Implement secure session management practices, including secure session storage and handling session tokens.
Authentication and Authorization:
Strong Password Policies: Enforce strong password requirements, multi-factor authentication (MFA), and account lockout policies.
Secure Authentication Protocols: Use secure authentication protocols (e.g., OAuth, OpenID Connect) and avoid storing plaintext passwords.
Data Encryption:
SSL/TLS Encryption: Ensure that data in transit is encrypted using secure protocols (SSL/TLS).
Data at Rest Encryption: Encrypt sensitive data stored in databases or other storage systems.
Cross-Site Scripting (XSS) Prevention:
Input Validation: Validate and sanitize user inputs to prevent malicious script injection.
Content Security Policy (CSP): Implement CSP headers to control which resources can be loaded and executed on a web page.
Cross-Site Request Forgery (CSRF) Protection:
Anti-CSRF Tokens: Include anti-CSRF tokens in forms to prevent unauthorized requests.
SameSite Cookies: Set SameSite attributes for cookies to mitigate CSRF attacks.
Security Headers:
HTTP Security Headers: Implement security headers, such as Strict-Transport-Security (HSTS), X-Content-Type-Options, and X-Frame-Options, to enhance overall security.
File Upload Security:
File Type Verification: Verify the file type before allowing uploads.
Restrictive Permissions: Limit file upload directories' permissions.
Security Patching:
Regular Updates: Keep all software components, including web servers, databases, and application frameworks, up-to-date with the latest security patches.
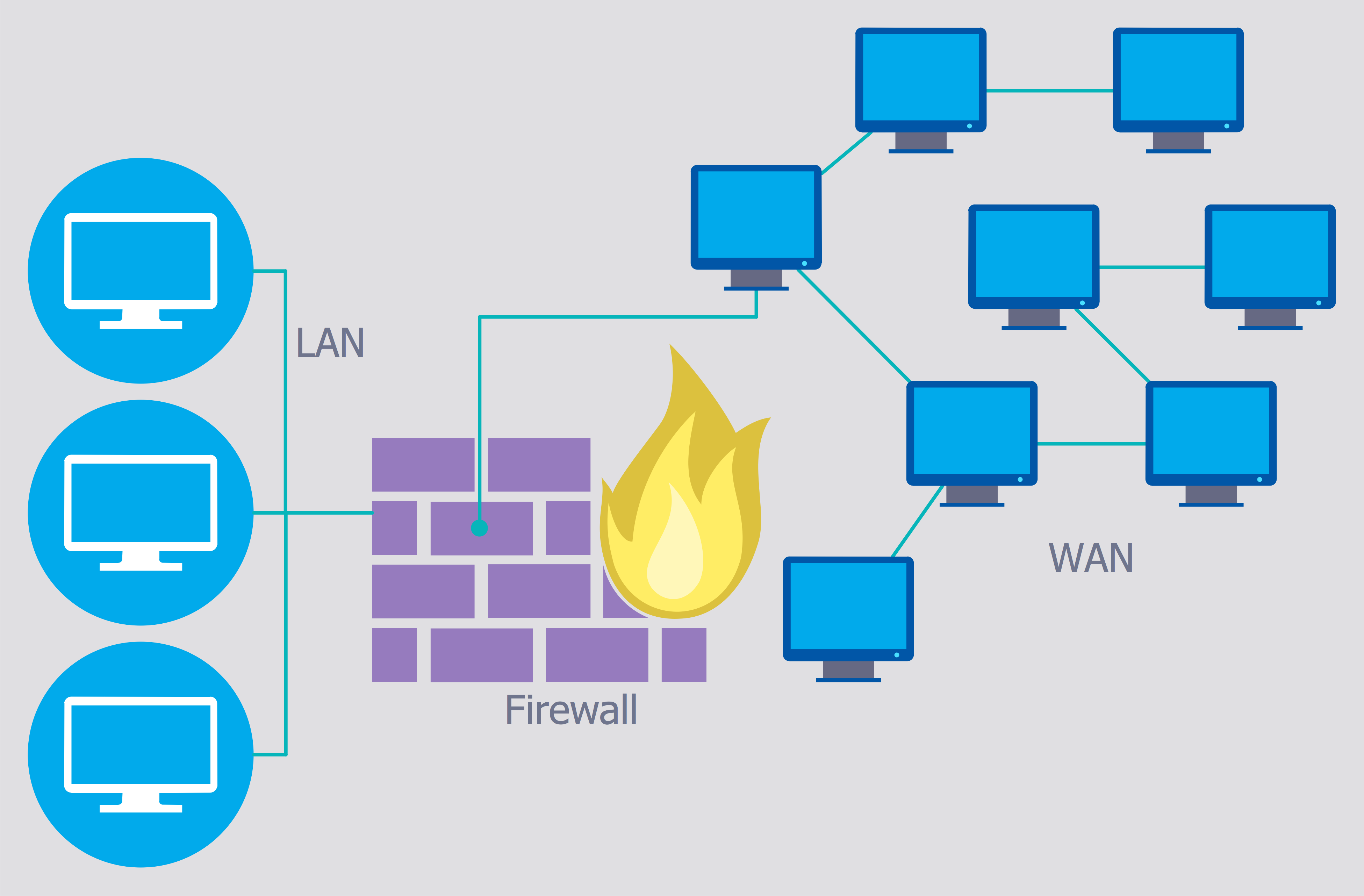
Network security
Network security is a crucial aspect of ethical hacking, as ethical hackers are tasked with identifying and addressing vulnerabilities in a network to improve its overall security. Here are key considerations and activities related to network security in the context of ethical hacking:
Vulnerability Assessment:
Ethical hackers conduct regular vulnerability assessments to identify weaknesses in the network infrastructure, including misconfigurations, outdated software, and potential entry points for attackers.
Penetration Testing:
Ethical hackers perform penetration testing, simulating real-world cyber attacks to assess the effectiveness of security controls. This involves attempting to exploit vulnerabilities in a controlled and ethical manner.
Firewall Testing:
Evaluate the configuration and effectiveness of firewalls. Ensure that rules and policies are correctly implemented to filter and monitor incoming and outgoing network traffic.
Intrusion Detection and Prevention Systems (IDPS) Testing:
Test the capabilities of IDPS to detect and respond to suspicious activities. Ethical hackers may attempt to trigger alerts and assess the system's response.
Wireless Network Security:
Assess the security of wireless networks by checking for encryption strength, proper authentication mechanisms, and vulnerabilities in wireless routers and access points.
Ethical and Professional Conduct:
Ethical hackers operate within a framework of ethical guidelines and legal boundaries. They prioritize integrity, honesty, and transparency in their actions.
Strong Technical Skills:
Proficiency in various technical areas, including network security, programming, operating systems, and cybersecurity tools, is essential for ethical hackers.
Curiosity and Inquisitiveness:
Ethical hackers are naturally curious and enjoy exploring systems to understand how they work. They have a keen interest in discovering vulnerabilities and improving security.
Continuous Learning:
The field of cybersecurity is dynamic, with new threats and technologies emerging regularly. Ethical hackers must stay up-to-date with the latest trends, tools, and techniques through continuous learning.
Analytical Thinking:
Ethical hackers need strong analytical skills to assess complex systems, identify vulnerabilities, and devise effective solutions. They must be able to think critically to understand and address security challenges.
Problem-Solving Skills:
Ethical hackers encounter various security issues that require creative and effective solutions. Strong problem-solving skills are crucial for successfully addressing and mitigating security vulnerabilities.
In conclusion, ethical hacking plays a pivotal role in fortifying digital ecosystems against the ever-evolving landscape of cyber threats. Ethical hackers, armed with technical prowess, analytical thinking, and a commitment to ethical and legal standards, serve as the vanguard in identifying and mitigating vulnerabilities within systems, networks, and applications.

The characteristics of ethical hackers, including curiosity, continuous learning, adaptability, and a keen sense of responsibility, define their approach to securing digital assets. Their commitment to ethical conduct ensures that their actions not only strengthen the cybersecurity posture of organizations but also maintain the trust and integrity of the broader digital community.





Post a Comment
0 Comments